Module 4: Secure Coding Practices for Input Validation
1.Range Validator control in ASP.NET supports which type?
A.Integer
B.String
C.Currency
D.All of the above
https://learn.microsoft.com/en-us/dotnet/api/system.web.ui.webcontrols.rangevalidator?view=netframework-4.8.1
2.Which approach does take less bandwidth and time to validate input data?
A.Server Side Validation
B.Client Side Validation
C.Remote Validation
D.Non of them
Client side validation is a process of validating user input on the client side, usually in the browser, before it is sent to the server. This approach takes less bandwidth and time to validate input data because the data is validated on the client side, before it is sent to the server.
This reduces the amount of data that needs to be sent to the server, and also reduces the amount of time it takes for the server to process the data. Additionally, client side validation can help reduce the risk of malicious input being sent to the server, as the data is validated before it is sent.
3.Which validation control is used to write client and server side code to validate the input value?
A.Required Field Validator
B.Range Validator
C.Custom Validator
D.Compare Validator
the Custom Validator is specifically designed to allow developers to write customized client side and server side code to validate user input.
4.Obtain an absolute path for the file or directory and convert all characters of path into its normal form in case of URI request.
A.Directory Traversal Attacks
B.XSS
C.CSRF
D.Sql Injection
Directory Traversal Attacks involve manipulating variables that reference files with "dot-dot-slash (../)" sequences and its variations or by using absolute file paths, which may allow such an attacker to access arbitrary files and directories stored on the system.
5.Which tool protects SQL injection as an entityframework internally uses paramterized query?
A.ADO.net
B.LINQ to SQL
C.ORM tool
D.Non of them
Object-Relational Mapping (ORM) tool, like the Entity Framework, automatically generates SQL for you and uses parameterized queries, thereby providing protection against SQL injection attacks.
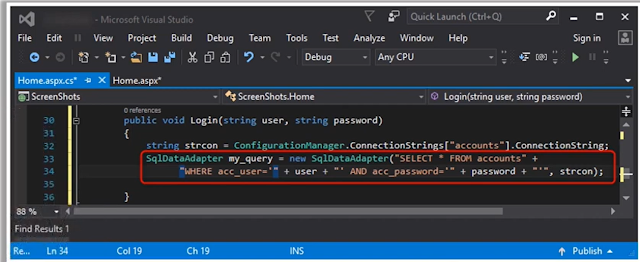
6.During his secure code review, John, an independent application security expert, found that the
developer has used C# code as highlighted in the following screenshot. Identify the security
mistake committed by the developer?
A. He is trying to use Whitelisting Input Validation
B. He is trying to use Non-parametrized SQL query
C. He is trying to use Blacklisting Input Validation
D. He is trying to use Parametrized SQL Query
7.Sam, an application security engineer working in INFRA INC., was conducting a secure code
review on an application developed in JAVA. He found that the developer has used a piece of
code as shown in the following screenshot. Identify the security mistakes that the developer has
coded?
A. He is attempting to use client-side validation
B. He is attempting to use whitelist input validation approach
C. He is attempting to use regular expression for validation
D. He is attempting to use blacklist input validation approach
8.Which approach is effective in defending against Cross-Site Scripting (XSS) attacks?
Response:
A. Filtering input data based on a blacklist of forbidden words
B. Validating and sanitizing all user input
C. Allowing all user inputs without validation for usability
D. Using only client-side input validation
9.Which of the following are common application-level attacks?
(Select two)
Response:
A. Phishing
B. SQL Injection
C. Denial of Service (DoS)
D. Cross-Site Scripting (XSS)
10.Which practice is NOT recommended to protect against XSS vulnerabilities?
Response:
A. Encoding output based on the context in the HTML page
B. Relying solely on browser-based XSS protection features
C. Sanitizing all user inputs, including those from authenticated users
D. Using Content Security Policy headers to reduce the risk of XSS
11.Which attack exploits poorly secured application inputs to alter database commands?
Response:
A. Cross-site scripting (XSS)
B. Denial of service (DoS)
C. SQL Injection
D. Phishing
12.How can developers prevent SQL Injection attacks in their web applications?
Response:
A. By using dynamic SQL with string concatenation
B. By implementing parameterized queries
C. By allowing direct user input in SQL queries
D. By avoiding the use of stored procedures
13.What is the impact of improper input validation on application security?
Response:
A. It has no impact on security
B. It can lead to vulnerabilities like SQL injection and cross-site scripting
C. It simplifies the application's UI
D. It reduces the application's storage requirements
14.Which of the following types of data should always be validated?
Response:
A. Data from trusted sources
B. Data from untrusted sources
C. Static data
D. Data that does not influence the application logic
15.How can input sanitization differ from input validation?
Response:
A. Sanitization alters the input to ensure its safety
B. Sanitization removes the need for validation
C. Sanitization increases the complexity of inputs
D. Sanitization is less important than validation
16.Which practices help in protecting sessions from XSS and CSRF attacks?
(Select two)
Response:
A. Enabling CORS on all server endpoints
B. Validating and sanitizing all user input
C. Using anti-forgery tokens in forms
D. Storing session IDs in client-side JavaScript variables
17.How can developers mitigate Open Redirect vulnerabilities in their web applications?
Response:
A. By strictly validating all redirect URLs against a whitelist
B. By allowing unrestricted redirects within the same domain
C. By relying on users to avoid clicking on suspicious links
D. By only permitting redirects to use HTTP, not HTTPS
防範點擊脅持的資安風險
18.How should an MVC application securely redirect a user after a successful login?
Response:
A. By redirecting to a fixed URL defined within the application's configuration
B. By using a parameter from the user's original request without validation
C. By validating and encoding the redirection URL to prevent open redirects
D. By allowing user input to dictate the redirection target without verification
MVC 應用程式在成功登入後應如何安全地重新導向使用者?若未驗證使用者的重導向參數,可能導致開放式重導向漏洞(Open Redirect),攻擊者可誘導使用者點擊惡意網站。必須對 URL 做驗證與編碼,確保其屬於允許的範圍。
19.Which is a common method to mitigate buffer overflow attacks in applications?
Response:
A. Data input validation
B. Using antivirus software
C. Installing security patches
D. Conducting penetration tests
常用的緩衝區溢位攻擊防範方法
緩衝區溢位的資安風險是由未限制輸入長度導致而成。因此有效的輸入驗證能限制輸入大小與格式,是預防此類漏洞的基本做法。
20.Why is input validation crucial in secure coding?
Response:
A. It enhances the aesthetic appeal of the application
B. It prevents malicious data from being processed
C. It is only necessary for output data
D. It increases the data processing time
為什麼輸入驗證在安全編碼中至關重要?
輸入驗證可防止惡意資料(如 SQL 指令、腳本)被系統執行,避免發生注入、XSS 等漏洞。
21.What is the risk of relying only on client-side input validation?
Response:
A. It ensures complete security
B. Client-side validation can be bypassed by attackers
C. It enhances server-side security automatically
D. There is no risk involved
僅依賴客戶端輸入驗證有什麼風險?
攻擊者可以透過開發者工具、Proxy 工具(如 Burp Suite)繞過前端驗證,因此伺服器端驗證是必要的。
22.What strategy should be employed to protect web applications from Parameter Tampering attacks?
Response:
A. Relying on client-side validation to detect tampered parameters
B. Using hidden fields to store sensitive data
C. Encrypting all parameters passed in URLs or forms
D. Trusting all user input if it comes from authenticated users
防止參數竄改(Parameter Tampering)攻擊的策略為何?
參數竄改是使用者修改 URL 或表單參數以竄改交易或資料,加密敏感參數並在後端驗證可有效避免這類攻擊。
23.Why is robust input validation crucial in web application security?
Response:
A. It enhances the user interface design.
B. It prevents a wide range of injection and other input-based attacks.
C. It improves application response time.
D. It increases the application's compatibility with different browsers.
為什麼穩健的輸入驗證對 Web 應用程式安全至關重要?
如 SQL injection、XSS、Command injection 等攻擊多源於未驗證或處理的輸入,因此強化輸入驗證能大幅降低這些風險。
24.Which methods help prevent Directory Traversal attacks?
(Select two)
Response:
A. Using absolute file paths for file access
B. Implementing proper input/output validation
C. Storing files outside the webroot
D. Disabling the server's file system
哪些方法有助於防止目錄遍歷(Directory Traversal)攻擊?
B:防止透過 ../ 類型字串跳出目錄範圍
C:避免直接存取 webroot 目錄下的重要檔案,降低誤導讀取敏感檔的風險。
25.Which techniques ensure secure input validation in ASP.NET Core applications?
(Select two)
Response:
A. Employing model binding
B. Using manual string parsing
C. Implementing client-side validation only
D. Applying server-side validation
在 ASP.NET Core 中,哪些技術可確保安全的輸入驗證?
Model binding:可自動將輸入資料對應到模型並驗證型別或屬性條件。
Server-side validation:是防範攻擊的核心,不能只依靠前端驗證。







留言
張貼留言