Module 3: Secure Application Design and Architecture
1.Which security design principle minimize the risk by reducing the number of entry point in an application?
A) Apply Defence in depth
B) Security through Obscurity
C) Reduce Attack Surface
D) Fail Securely
'Apply Defence in depth' is a principle that suggests multiple levels of security controls should be placed throughout an IT system.
'Security through Obscurity' is a principle that suggests security can be achieved by hiding the system or system's design.
'Fail Securely' is a concept where an application should handle errors by shifting to a state that prevents unintended access or data exposure.
2.In which threat modelling phase application is decomposed, and its entry points are reviewed from an attacker's perspective?
A) Control Recommendations
B) Impact Analysis
C) Threat Identification
D) Attack Surface Evaluation
Control Recommendations phase involves the process of recommending controls to deal with potential threats.
Impact Analysis involves determining the potential consequences of a threat.
Threat Identification simply involves recognizing potential threats to the application.
3.What defines the application's dependency on outside entities such as servers ,firewalls, security policies,os ,network etc.
A) External Dependecies
B) Enumerate Entry points
C) Enumerate Trust Levels
D) Enumerate Assets
External Dependencies in an application refer to any dependency of the system that comes from outside, such as servers, firewalls, security policies, network setup, etc. Assessing these dependencies is vital to understanding the overall architecture and potential vulnerabilities in an application.
enumerating entry points refers to identifying all possible ways an attacker can enter the system, such as exposed APIs, Form submissions, and many more.
enumerating trust levels means identifying different access levels within an application, such as user access, admin access, etc.
enumerating assets involves identifying the valuable data or services of the system that an attacker might be interested in.
4.In which phase of secure development lifecycle the threat modeling is performed?
A. Coding phase
B. Testing phase
C. Deployment phase
D. Design phase
5.Which of the threat classification model is used to classify threats during threat modeling process?
A. RED
B. STRIDE
C. DREAD
D. SMART
6.Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
A. DREAD
B. SMART
C. STRIDE
D. RED
威脅建模(Threat Modeling)中的風險評估模型為何者?
DREAD 模型 是一種用來「評分風險大小」的模型,常搭配 STRIDE 使用。
DREAD 是縮寫,代表五個維度(各項打分數,通常為 1 至 10 分,數值越高表示風險越大。):
- Damage Potential:攻擊成功會造成多大損害?
- Reproducibility:攻擊有多容易重現?
- Exploitability:攻擊多容易被執行?
- Affected Users:受影響的使用者數量?
- Discoverability:攻擊者有多容易發現這個漏洞?
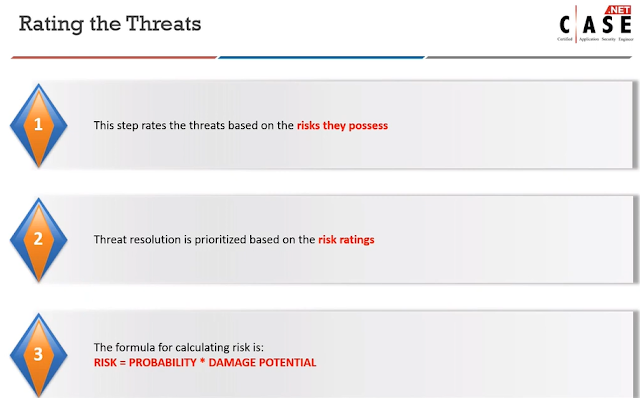
7.Identify the formula for calculating the risk during threat modeling.
A. RISK = PROBABILITY *Attack
B. RISK = PROBABILITY * ASSETS
C. RISK = PROBABILITY * DAMAGE POTENTIAL
D. RISK = PROBABILITY * VULNERABILITY
8.What is the primary purpose of threat modeling in secure application design?
Response:
A. To ensure the application is user-friendly
B. To identify potential security threats and vulnerabilities
C. To enhance the performance of the application
D. To facilitate marketing strategy development
Ref:





留言
張貼留言