Module 7: Secure Coding Practices for Session Management
1.Which is not the common threats to session management?
A.CSRF
B.XSS
C.Token Brute-Force Attack
D.Token Maniulation Attack
XSS (Cross-Site Scripting) is a type of attack that injects malicious code into a web application. It is not a threat to session management, as it does not directly target the session itself.
Instead, XSS attacks are used to gain access to sensitive information, such as user credentials, by exploiting vulnerabilities in the application code. XSS attacks can be used to hijack user sessions, but they are not a direct threat to session management.
CSRF攻擊
2.Which is not the type of client side session management?
A.Cookies
B.Query String
C.Profile
D.ViewState
Option C is CORRECT because profile is not a type of client-side session management. The profile is a component of ASP.NET for storing user-specific data on the server-side, not the client-side.
3.Which is default session mode?
A.InProc
B.SqlServer
C.StateServer
D.Custom
Option A is CORRECT because InProc is the default session mode in .NET. InProc mode stores session state values and variables in memory on the local IIS web server and is generally the fastest method.
也不利於導入cluster分散式架構(web gardens , web farms)
另一種mode: StateServer只支援本機AD
4.What should be not logged?
A.Entire database or table
B.Legal and other opts in
C.Application errors and system events
D.input and output validation filters
Option A is CORRECT because logging an entire database or table can potentially expose sensitive information, it can also lead to storage or processing issues due to the large amount of data. It is therefore not advisable from a security and performance perspective.
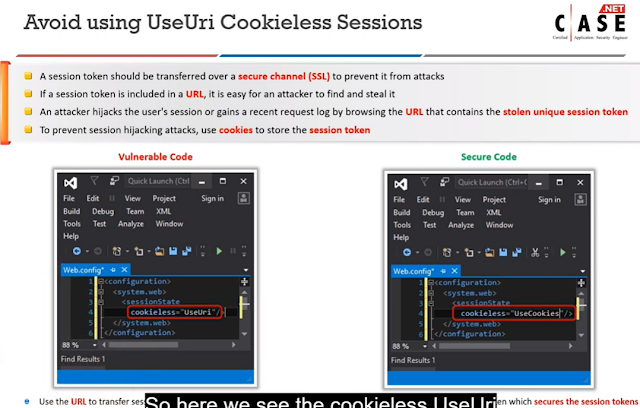
5.Which is the best approach to store the session tokens?
A.UseURI
B.UseCookies
C.DeviceUse
D.Non of them
Using cookies to store session tokens is the best approach because it is the most secure way to store session tokens. Cookies are stored on the user's computer, which means that the session tokens are not stored on the server. This makes it more difficult for malicious actors to access the session tokens, as they would need to gain access to the user's computer.
Additionally, cookies are encrypted, which adds an extra layer of security. Finally, cookies are also more efficient than other methods of storing session tokens, as they can be quickly accessed and updated.
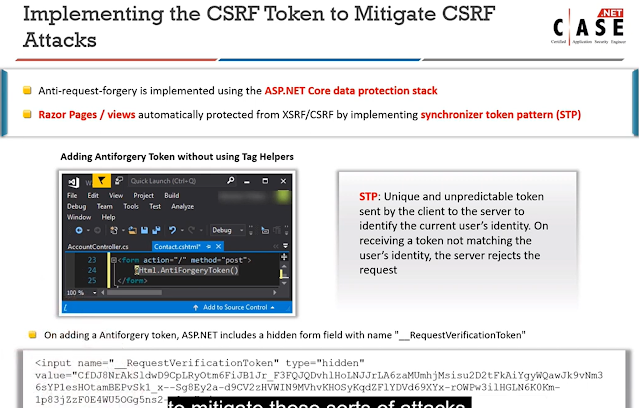
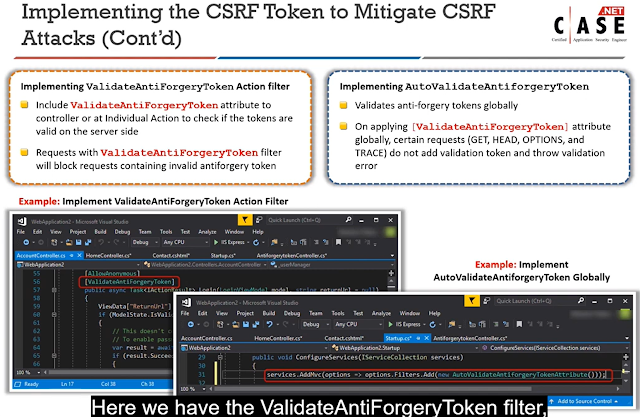
6.Which practices help in protecting sessions from XSS and CSRF attacks?
(Select two)
Response:
A. Enabling CORS on all server endpoints
B. Validating and sanitizing all user input
C. Using anti-forgery tokens in forms
D. Storing session IDs in client-side JavaScript variables
7.Why should session tokens be stored securely on the client side?
Response:
A. To ensure they are easily accessible to third parties
B. To prevent unauthorized access and use of session tokens
C. Storage security has no impact on session tokens
D. To make session management more complex
會很容易被預測破解。
8.What is an effective method to secure ViewState from session attacks?
Response:
A. Disabling ViewState entirely for all applications
B. Encrypting and validating ViewState data
C. Storing ViewState data in a centralized database
D. Using ViewState only over unencrypted connections
9.How can session fixation be prevented?
要如何防止「會話固定攻擊(Session Fixation)」?
Response:
A. By fixing the session ID after the user logs in
B. By allowing users to choose their session IDs
C. Regenerating a new session ID upon authentication
D. Using predictable session IDs
Session Fixation(會話固定攻擊) 是指:
攻擊者事先給使用者一個已知的 Session ID,等使用者登入後直接盜用這個已知 Session。
防護方法:
✅ 使用者登入成功後,立刻重新產生新的 Session ID!
✅ Session ID 必須不可預測(隨機且夠長)。
✅ 設置 Secure、HttpOnly cookie 屬性。
10.What mechanism can help in detecting session hijacking attempts?
哪一種機制有助於偵測會話劫持(Session Hijacking)攻擊?
Response:
A. Ignoring abrupt changes in the client's IP address or User-Agent during a session
B. Binding the session to specific IP addresses
C. Allowing unlimited session lifetime
D. Encouraging users to write down their session IDs for backup
B.將會話綁定到特定 IP 地址可以幫助偵測或阻止會話劫持(因為劫持者通常 IP 不同)。
A.應該注意IP或User-Agent的異常變動,忽略的話反而讓攻擊更難發現。
C.讓 Session 永不過期會增加被劫持的風險,反而降低安全性。
D.Session ID 必須保密,寫下來是重大資安風險!
"綁 IP 防劫持,變動警示要注意。"
"Session ID 要保密,不可隨便記錄!"
在EC Council教材中也有提供如下的建議防範實踐措施
11.What is a key defensive coding practice to prevent session hijacking?
Response:
A. Transmitting session IDs over insecure channels to ensure availability
B. Using secure and HttpOnly cookies for session management
C. Allowing users to choose their session IDs for personalization
D. Storing session data in local storage for easy retrieval
12.In ASP.NET Core, what is a recommended practice for session management?
Response:
A. Disabling session state entirely to prevent attacks
B. Storing sensitive information in session state
C. Protecting session cookies with appropriate flags such as Secure and HttpOnly
D. Allowing session cookies to be accessed via client-side scripts
13.How can developers mitigate the risk of session replay and fixation attacks?
Response:
A. By accepting session IDs from query strings or form fields without validation
B. Implementing strict session validation and regeneration strategies
C. Using only client-side scripts to manage session lifecycles
D. Encouraging users to use shared computers for accessing the application
Session Replay:是用戶自己的合法 Session 被偷來複製使用。
攻擊者在使用者登入後,重複發送舊封包來轉帳。偷封包,重播行為。
Session Fixation:是攻擊者安排的 Session ID,被受害者不知情使用。
攻擊者讓使用者用他指定的 Session ID 登入後,再接管帳戶。
事先安排 Session ID,釣受害者上鉤。
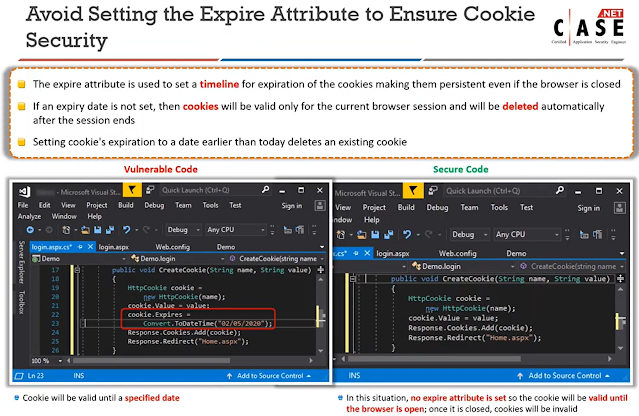
因為SessionID cookie會存放於user的browser當中,若沒有去設置時間失效也仍有安全疑慮。
左邊(登入 Login 畫面程式碼)
主要流程:
(1)驗證使用者帳密 (Membership.ValidateUser)。
(2)如果驗證成功:
- 使用 FormsAuthentication.SetAuthCookie 設定新的認證 Cookie(標準做法)。
- Session["LoggedIn"] 設定成功登入狀態。
- 用 RNGCryptoServiceProvider 產生一個安全的隨機數組(AuthID)。
- 將這個隨機數(經過 Base64 編碼)設定到一個新的 Http Cookie,名字叫 "AuthToken"。
(3)最後重新導向到 /Default.aspx。
重點(防止 Session Fixation)
- 每次登入成功時,產生新的隨機 Authentication Token。
- 這個 Token 綁定在使用者 Session 上,確保不是攻擊者事先植入的 Session ID。
右邊(登出 Logout 畫面程式碼)
主要流程:
(1)清除 Session (Session.Clear()、Session.Abandon()、Session.RemoveAll())。
(2)檢查是否存在 Session ID 的 Cookie(ASP.NET_SessionId):
- 如果存在,把它設成空白字串,並讓它過期(Expires 設定為過去時間)。
(3)檢查是否存在 Authentication Token(AuthToken):
- 同樣清空值,設定過期時間,讓它失效。
重點(防止 Session Fixation)
- 確保登出時完全刪除舊的 Session ID 與 Auth Token Cookie。
- 避免攻擊者重用被竊取或固定的 Session。
14.Which session management technique is considered insecure?
Response:
A. Storing session identifiers in encrypted cookies
B. Passing session identifiers in the URL
C. Regenerating session IDs at authentication
D. Implementing session expiration policies
15.Why is secure session management critical in web applications?
Response:
A. It enhances the user interface and user experience.
B. It prevents unauthorized access to user sessions.
C. It increases the application's loading speed.
D. It aids in the marketing analysis of user behavior.
16.What is a secure practice for managing user sessions in web applications?
Response:
A. Allowing indefinite session durations
B. Implementing session timeouts and expiration
C. Storing session IDs in easily accessible locations
D. Reusing session IDs across multiple sessions















































留言
張貼留言