AZ-305_Azure Solution Architect學習筆記_Azure identity, access, and security
Microsoft Entra ID
Microsoft Entra ID 是一項基於雲端的身分識別與存取管理服務,能夠安全地登入並存取 Microsoft 雲端應用程式及自訂的雲端應用程式。它可與本地端 Active Directory 整合,適用於混合環境。
Active Directory in On-Premises Environments
本地端環境中的 Active Directory
運行於 Windows Server 的本地端 Active Directory 提供身分識別與存取管理,由組織內部管理。它與 Microsoft Entra ID 互補,以實現全球可用性。
Securing Identities with Microsoft Entra ID
使用 Microsoft Entra ID 保護身份安全
Microsoft Entra ID 偵測來自未知裝置或地點的可疑登入嘗試,提升安全性,超越本地 Active Directory 的功能。
Who Uses Microsoft Entra ID?
誰在使用 Microsoft Entra ID?
IT 管理員管理存取權限,應用程式開發人員啟用單一登入(SSO)和身份驗證,使用者維護其憑證,線上服務訂閱者則使用 Microsoft Entra ID 進行身份驗證。
Key Features of Microsoft Entra ID
Microsoft Entra ID 的主要功能
- Authentication: Verifies identities, supports MFA, password resets, and smart lockouts.
身份驗證:驗證身份,支援多重身份驗證(MFA)、密碼重設及智慧鎖定。 - Single Sign-On (SSO): Simplifies access by linking a single identity to multiple applications.
單一登入(SSO):透過將單一身份連結至多個應用程式,簡化存取流程。 - Application Management: Offers tools for managing apps, including SaaS integration and My Apps portal.
應用程式管理:提供管理應用程式的工具,包括 SaaS 整合及 My Apps 入口網站。 - Device Management: Enables device registration and policy enforcement with Conditional Access.
裝置管理:啟用裝置註冊及條件式存取的政策執行。
Connecting On-Premises AD to Microsoft Entra ID
將本地端 AD 連接至 Microsoft Entra ID
使用 Microsoft Entra Connect,可將本地端 AD 身份同步至 Microsoft Entra ID。這支援兩個系統間的無縫單一登入(SSO)、多重身份驗證(MFA)及其他進階功能。
Microsoft Entra Domain Services
Microsoft Entra 網域服務
提供受管網域服務,如網域加入、群組原則、LDAP 以及 Kerberos/NTLM 認證。它支援舊有應用程式,無需專用的網域控制器。
Benefits of Microsoft Entra Domain Services
Microsoft Entra 網域服務的優點
- Legacy Support: Lift and shift legacy applications to Azure while maintaining existing credentials.
舊有支援:將舊有應用程式遷移至 Azure,同時維持現有的憑證。 - Integration: Synchronizes user data from Microsoft Entra ID, enabling seamless access for existing users and groups.
整合性:從 Microsoft Entra ID 同步使用者資料,讓現有使用者和群組能無縫存取。
How Microsoft Entra Domain Services Works
Microsoft Entra 網域服務的運作方式
受管網域包含由 Azure 部署的 Windows Server 網域控制器。這些控制器由 Azure 完全管理,包括更新、備份和加密。
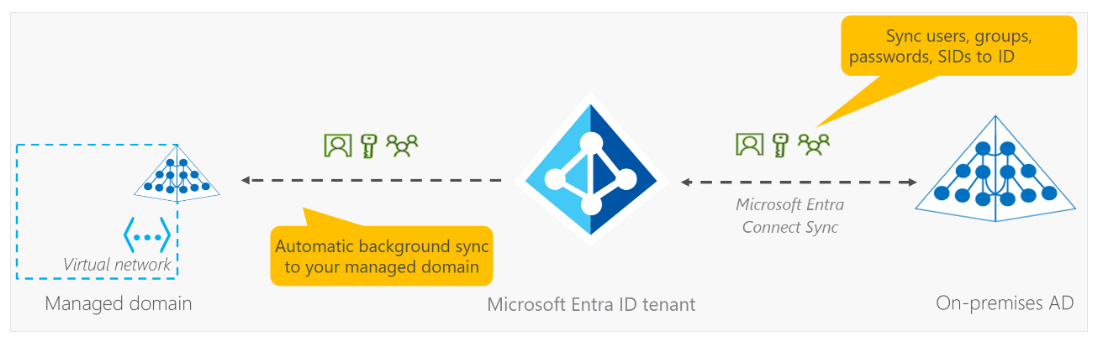
Synchronization in Managed Domains
受管網域中的同步
從 Microsoft Entra ID 到 Microsoft Entra 網域服務的一向同步確保資料一致性。內部部署的 AD 資料透過 Entra Connect 同步到 Entra ID,然後再同步到受管網域。
Azure Authentication Methods
Azure 認證方法
Azure 提供多種認證方法來確認使用者、服務或裝置的身份。這些方法包括標準密碼、單一登入(SSO)、多重身份驗證(MFA)以及無密碼認證。
Single Sign-On (SSO) 單一登入(SSO)
SSO 允許使用者只需登入一次,即可存取多個資源而無需重新驗證。它簡化了密碼管理,並降低了與憑證相關的安全風險。
Multifactor Authentication (MFA)
多重身份驗證(MFA)
MFA 透過要求兩個或以上的驗證因素,例如密碼、手機代碼或生物識別資料,來增強安全性。這降低了憑證被盜用的風險。
Microsoft Entra Multifactor Authentication
Microsoft Entra 多重身份驗證
此 Microsoft 服務提供 MFA 功能,選項包括電話通話、應用程式通知或代碼。它為登入增加額外的安全層。
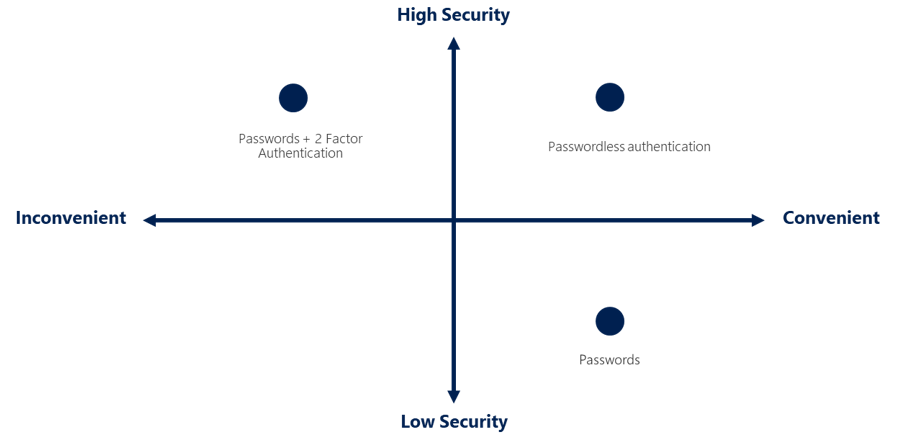
Passwordless Authentication
無密碼驗證
無密碼方法消除了傳統密碼,改用裝置、生物特徵或 PIN 碼進行驗證。此方法提升了安全性與使用者便利性。
Windows Hello for Business
Windows Hello for Business 使用與特定電腦綁定的生物特徵或 PIN 碼進行無密碼驗證。它支援單一登入(SSO)並整合企業資源。
Microsoft Authenticator App
Microsoft Authenticator 應用程式
該應用程式將手機轉變為安全的驗證裝置。它支援使用生物識別或 PIN 進行無密碼登入,並確保跨平台的無縫存取。
FIDO2 Security Keys FIDO2 安全金鑰
FIDO2 安全金鑰是提供無密碼驗證的硬體裝置。它們透過消除密碼並利用如 WebAuthn 等標準來提升安全性。
Azure External Identities
Azure 外部身份識別
Azure 外部身份識別允許與組織外的人員、裝置或服務(包括合作夥伴、供應商和客戶)進行安全互動。它們透過讓外部使用者存取您的資源來支援協作。
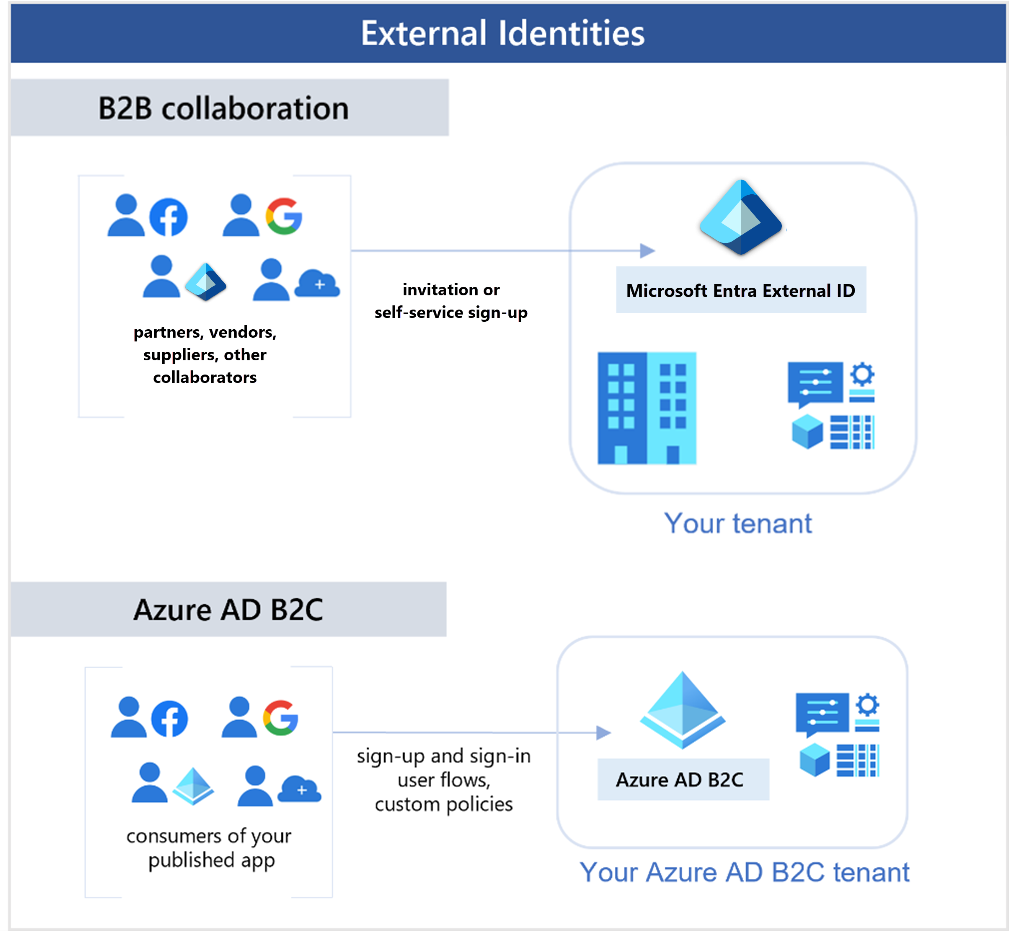
External Users "Bring Their Own Identities"
外部使用者「自帶身份」
外部使用者可以使用他們的憑證登入,例如企業、政府發行或社交身份(如 Google 或 Facebook)。他們的身份由其身份提供者管理,而您則使用 Microsoft Entra ID 或 Azure AD B2C 管理應用程式存取權限。
Business-to-Business (B2B) Collaboration
企業對企業(B2B)協作
B2B 協作允許外部使用者使用他們偏好的身份存取您的 Microsoft 應用程式和企業應用程式。這些使用者通常以來賓使用者的身份存在於您的目錄中。
B2B Direct Connect B2B 直接連接
直接連接與另一個 Microsoft Entra 組織建立雙向信任,實現無縫協作,例如透過 Teams 共享頻道。這些使用者不在您的目錄中,但可以透過 Teams 管理工具進行管理。
Business-to-Customer (B2C) Collaboration
企業對消費者(B2C)協作
Azure AD B2C 允許您管理使用現代 SaaS 應用程式或自訂開發應用程式的消費者身份和存取,為面向客戶的應用程式提供安全且可擴展的解決方案。
Access Reviews for Guest Users
來賓使用者的存取審查
管理員或決策者可以執行存取審查,以確保來賓使用者擁有適當的權限。Microsoft Entra ID 提供建議,並可撤銷不必要的存取權限以維護安全。
Azure Conditional Access Azure 條件式存取
Azure 條件式存取是 Microsoft Entra ID 的一項工具,會評估身份訊號,例如使用者身份、位置和裝置,以決定是否授予資源存取權限。它在保護組織資產的同時,平衡生產力與安全性。
Granular Multi-Factor Authentication (MFA)
細緻的多重身份驗證 (MFA)
條件式存取提供量身打造的 MFA 體驗。例如,位於已知位置的使用者可以免除額外檢查,而位於異常位置的使用者則可能需要提供第二道驗證因素。
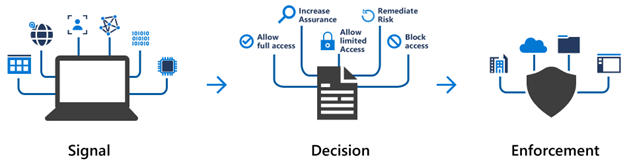
Signal, Decision, and Enforcement
訊號、決策與執行
條件式存取在登入過程中收集訊號(例如,使用者位置或裝置),根據這些訊號做出決策,並執行授權、拒絕或挑戰存取等動作。
Key Use Cases for Conditional Access
條件式存取的主要使用案例
- Require MFA Based on Context: Enforce MFA for administrators or external network users.
根據情境要求多重身份驗證(MFA):對管理員或外部網路使用者強制執行多重身份驗證。 - Restrict Access to Approved Applications: Limit access to specific, compliant client applications.
限制僅允許核准的應用程式存取:限制存取至特定且符合規範的用戶端應用程式。 - Ensure Access from Managed Devices: Allow only devices meeting security and compliance standards.
確保僅由受管理的裝置存取:僅允許符合安全與合規標準的裝置。 - Block Access from Untrusted Sources: Deny access from unknown or high-risk locations.
阻擋來自不受信任來源的存取:拒絕來自未知或高風險地點的存取。
Azure Role-Based Access Control (Azure RBAC)
Azure 角色型存取控制 (Azure RBAC)
Azure RBAC allows you to control access to cloud resources by assigning roles with specific permissions. It helps implement the principle of least privilege, granting only the access required to complete a task.
Azure RBAC 允許您透過指派具有特定權限的角色來控制對雲端資源的存取。它有助於實施最小權限原則,只授予完成任務所需的存取權限。
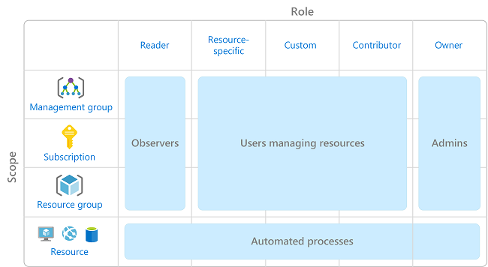
Built-In and Custom Roles
內建角色與自訂角色
Azure provides built-in roles for common access needs and allows you to define custom roles. Assigning users or groups to roles ensures consistent access permissions for existing and new resources.
Azure 提供內建角色以滿足常見的存取需求,並允許您定義自訂角色。將使用者或群組指派到角色,可確保現有及新資源的存取權限一致。
Role Assignments and Scopes
角色指派與範圍
Roles are assigned to scopes, which can include management groups, subscriptions, resource groups, or individual resources. Permissions granted at a parent scope are inherited by all child scopes.
角色會被指派到範圍,範圍可以包括管理群組、訂閱、資源群組或個別資源。在父範圍授予的權限會被所有子範圍繼承。
Hierarchical Permissions 階層式權限
Azure RBAC is hierarchical; for example, assigning the Owner role at the management group scope allows control over all subscriptions in that group. Similarly, assigning the Reader role at the subscription level allows viewing all resources within it.
Azure RBAC 是階層式的;例如,在管理群組範圍指派擁有者角色,便可控制該群組內的所有訂閱。同樣地,在訂閱層級指派讀者角色,則可檢視該訂閱內的所有資源。
Enforcement Through Azure Resource Manager
透過 Azure Resource Manager 強制執行
Azure RBAC permissions are enforced through Azure Resource Manager. It controls actions performed via the Azure portal, CLI, PowerShell, or Cloud Shell, but does not handle application or data-level security.
Azure RBAC 權限是透過 Azure Resource Manager 強制執行的。它控制透過 Azure 入口網站、CLI、PowerShell 或 Cloud Shell 執行的操作,但不處理應用程式或資料層級的安全性。
Allow Model of Azure RBAC
Azure RBAC 的允許模型
Azure RBAC operates on an "allow" model. If multiple role assignments grant overlapping permissions, users receive the combined permissions for the specified resource or scope.
Azure RBAC 採用「允許」模型。如果多個角色指派授予重疊的權限,使用者將獲得指定資源或範圍的合併權限。
Zero Trust Model 零信任模型
Zero Trust is a security model that assumes breach from the outset and protects resources by verifying every request. It treats every access attempt as though it originates from an uncontrolled network, requiring continuous authentication.
零信任是一種安全模型,從一開始就假設系統可能遭到入侵,並透過驗證每一個請求來保護資源。它將每一次存取嘗試視為來自不受控網路,因而需要持續進行身份驗證。
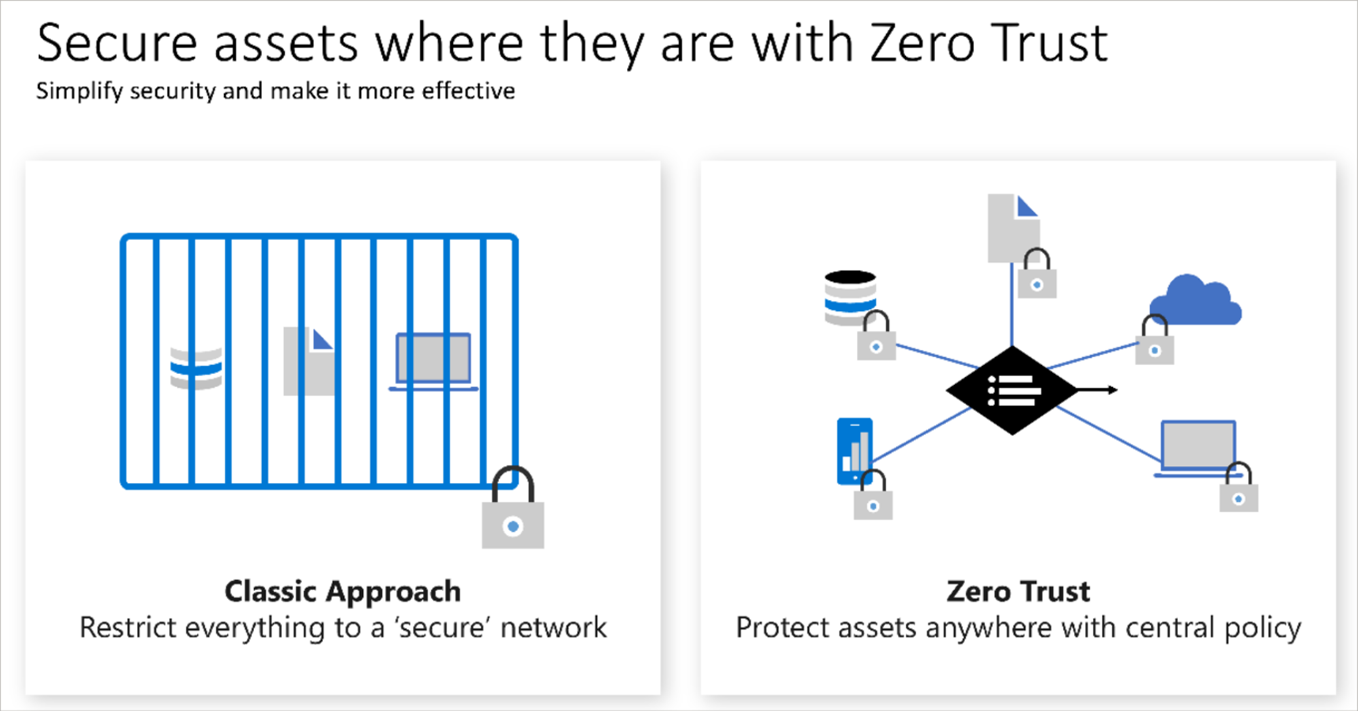
Need for Zero Trust 零信任的必要性
Modern environments demand a security approach that adapts to mobile workforces and distributed systems. Zero Trust safeguards people, devices, applications, and data irrespective of their location.
現代環境需要一種能適應行動工作者和分散式系統的安全方法。Zero Trust 不論人員、裝置、應用程式或資料位於何處,都能提供保護。
Key Principles of Zero Trust
Zero Trust 的關鍵原則
- Verify Explicitly: Authenticate and authorize based on all available data points.
明確驗證:根據所有可用的數據點進行身份驗證和授權。 - Least Privilege Access: Provide minimal access with JIT/JEA policies and risk-based adaptive controls.
最小權限存取:透過 JIT/JEA 政策及基於風險的自適應控制,提供最低限度的存取權限。 - Assume Breach: Segment access, encrypt data, and utilize analytics for threat detection.
假設已遭入侵:分段存取、加密資料,並利用分析進行威脅偵測。
Traditional vs. Zero Trust
傳統模型與零信任
Traditional models rely on the safety of corporate networks, assuming internal devices are secure. Zero Trust shifts to authenticating every device and user, granting access based on credentials instead of location.
傳統模型依賴企業網路的安全,假設內部裝置是安全的。零信任則轉向驗證每一個裝置和使用者,根據憑證而非位置授予存取權限。
Defense-in-Depth 深度防禦
Defense-in-depth is a security strategy designed to protect information by employing multiple layers of defense mechanisms. The objective is to slow attackers and provide alerts to security teams, reducing the reliance on any single layer.
深度防禦是一種安全策略,旨在透過多層防禦機制來保護資訊。其目標是延緩攻擊者的行動並向安全團隊發出警報,減少對任何單一層級的依賴。
Layers of Defense-in-Depth
深度防禦的層級
Defense-in-depth comprises multiple layers such as data, application, compute, network, perimeter, identity & access, and physical security. These layers work together to ensure comprehensive protection.
深度防禦包含多個層級,如資料、應用程式、運算、網路、邊界、身分與存取,以及實體安全。這些層級協同運作,以確保全面的保護。
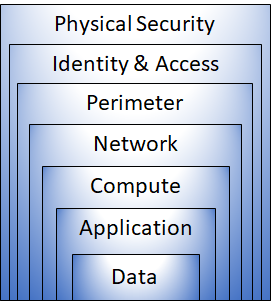
Physical Security 實體安全
This is the first line of defense, involving secure access to buildings and computing hardware in data centers. It prevents bypassing other layers and handles theft or loss effectively.
這是第一道防線,涉及對數據中心建築物和計算硬體的安全存取。它防止繞過其他層級,並有效處理竊盜或遺失問題。
Identity and Access 身份與存取
This layer focuses on securing identities and controlling access. Features like single sign-on (SSO), multifactor authentication, and event auditing ensure controlled access and change monitoring.
此層專注於保護身份和控制存取。像是單一登入(SSO)、多重身份驗證以及事件稽核等功能,確保存取受控並監控變更。
Perimeter 周邊防護
The perimeter layer defends against network-based attacks using tools like DDoS protection and perimeter firewalls. It identifies, eliminates, and alerts about malicious threats.
邊界層使用像是 DDoS 防護和邊界防火牆等工具來防禦基於網路的攻擊。它能識別、消除並警示惡意威脅。
Network 網路
This layer limits resource communication to reduce the spread of attacks. Key practices include denying by default, restricting inbound/outbound internet access, and implementing secure connectivity.
此層限制資源間的通訊,以減少攻擊的擴散。主要做法包括預設拒絕、限制進出網際網路的存取,以及實施安全連線。
Compute 運算
The compute layer ensures the security of virtual machines and endpoints. It includes malware protection, patch management, and securing access to compute resources.
計算層確保虛擬機器和端點的安全。它包括惡意軟體防護、補丁管理以及保護對計算資源的存取。
Application 應用程式
Secure application development reduces vulnerabilities. Practices include storing sensitive secrets securely, designing security into applications, and ensuring vulnerability-free code.
安全的應用程式開發可降低漏洞風險。做法包括安全儲存敏感機密、在應用程式中設計安全機制,以及確保程式碼無漏洞。
Data 資料
The data layer focuses on securing business and customer data. Key measures include encryption, secure storage, and meeting regulatory compliance for confidentiality, integrity, and availability.
資料層專注於保護企業和客戶資料的安全。主要措施包括加密、安全儲存,以及符合機密性、完整性和可用性的法規要求。
Microsoft Defender for Cloud
Defender for Cloud is a robust security tool for monitoring and improving your cloud and on-premises security posture. It provides guidance and notifications to help secure hybrid, multi-cloud, and on-premises environments seamlessly.
Defender for Cloud 是一款強大的安全工具,用於監控並提升您的雲端及本地端安全狀態。它提供指導和通知,幫助無縫保護混合雲、多雲及本地環境。
Protection Across Environments
跨環境的保護
Defender for Cloud monitors Azure services natively and extends to on-premises and multi-cloud resources. Azure Arc enables integration for hybrid environments, ensuring complete security coverage.
Defender for Cloud 原生監控 Azure 服務,並擴展至本地端及多雲資源。Azure Arc 支援混合環境整合,確保完整的安全覆蓋。
Azure-Native Threat Detection
Azure 原生威脅偵測
Defender for Cloud detects threats targeting Azure PaaS services, SQL databases, and networks. It offers anomaly detection, vulnerability assessments, and just-in-time VM access to secure resources effectively.
Defender for Cloud 偵測針對 Azure PaaS 服務、SQL 資料庫及網路的威脅。它提供異常偵測、漏洞評估及即時虛擬機存取,能有效保護資源安全。
Hybrid and Multicloud Protection
混合與多雲防護
Beyond Azure, Defender for Cloud secures on-premises and other cloud environments (e.g., AWS, GCP). It uses tools like Azure Arc and advanced plans to provide comprehensive threat protection.
除了 Azure 之外,Defender for Cloud 也保護本地端和其他雲端環境(例如 AWS、GCP)。它利用 Azure Arc 和進階方案等工具,提供全面的威脅防護。
Continuous Assessment 持續評估
Defender for Cloud continuously assesses security posture, identifying vulnerabilities in VMs, SQL servers, and containers. It integrates with Microsoft Defender for Endpoint for seamless vulnerability management.
Defender for Cloud 持續評估安全狀態,識別虛擬機、SQL 伺服器和容器中的漏洞。它與 Microsoft Defender for Endpoint 整合,實現無縫的漏洞管理。
Security Policies and Recommendations
安全政策與建議
Built on Azure Policy, Defender for Cloud enforces security policies across subscriptions and tenants. It provides prioritized recommendations aligned with the Azure Security Benchmark to reduce attack surfaces.
Defender for Cloud 建立在 Azure Policy 之上,能在訂閱和租戶間強制執行安全政策。它提供與 Azure 安全基準相符的優先建議,以降低攻擊面。
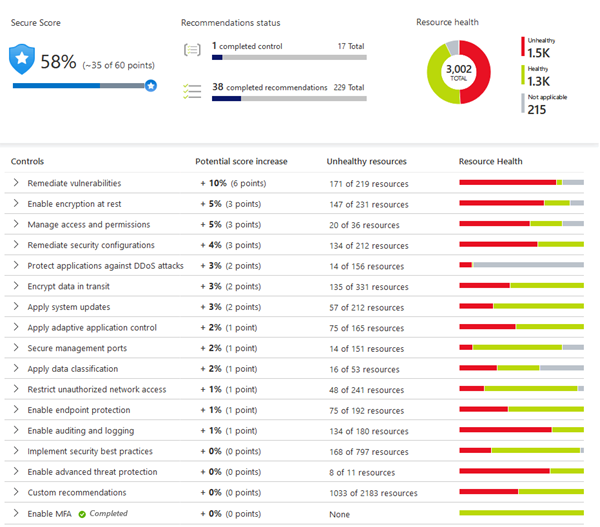
Secure Score and Controls
安全分數與控管
The secure score offers a quick view of your security posture. Recommendations are grouped into controls, helping prioritize improvements and maintain compliance with best practices.
安全分數提供您安全狀態的快速概覽。建議會依控管分組,有助於優先改善並維持符合最佳實務的合規性。
Advanced Threat Protection
進階威脅防護
Defender for Cloud provides advanced features like just-in-time VM access, adaptive application controls, and network hardening to defend against sophisticated threats and unauthorized access.
Defender for Cloud 提供進階功能,如即時虛擬機存取、自適應應用程式控制及網路強化,以防禦複雜威脅和未經授權的存取。
Security Alerts and Automation
安全警示與自動化
When threats are detected, Defender for Cloud generates detailed alerts with remediation steps. Integrated fusion kill-chain analysis and automation options streamline responses to complex attacks.
當偵測到威脅時,Defender for Cloud 會產生包含修復步驟的詳細警示。整合的融合攻擊鏈分析與自動化選項,簡化了對複雜攻擊的回應流程。



留言
張貼留言