經典ASP_表單提交參數語法及編碼校正_網址傳參數顯示於網頁中會中文亂碼的問題排除
近期又回到考古學者的身分
開始又接觸到Active Server Page 跟 Crystal Report
剛好在第二份工作都有摸過這些老東西XDD
稍微溫故 暖身
筆記一下
程式碼
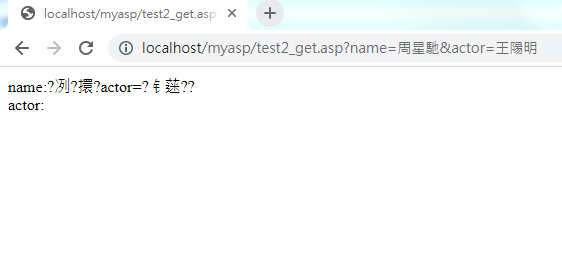
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | <HTML> <HEAD> </HEAD> <BODY> <% name = Request("name") Response.write "name:" & name & "<br />" name1 = Request("actor") Response.write "actor:" & name1 & "<br />" %> </BODY> </HTML> |
Step1.先調整此頁程式碼的codepage
codepage指定了IIS按什麼編碼讀取傳遞過來的串串(表單提交,地址欄傳遞等)。
在此先改為UTF8
讓沒按照key1=val1&key2=val2方式作正確擷取可排除
程式碼
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <%@ codepage=65001%> <HTML> <HEAD> </HEAD> <BODY> <% name = Request("name") Response.write "name:" & name & "<br />" name1 = Request("actor") Response.write "actor:" & name1 & "<br />" %> </BODY> </HTML> |
Step2. charset 用來指定網頁內容是用什麼編碼
在此設置UTF8 瀏覽器就會以 UTF-8 來載入
程式碼
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <%@ codepage=65001%> <HTML> <HEAD> <meta http-equiv="content-type" content="text/html; charset=utf-8"> </HEAD> <BODY> <% name = Request("name") Response.write "name:" & name & "<br />" name1 = Request("actor") Response.write "actor:" & name1 & "<br />" %> </BODY> </HTML> |
Ref:
https://medium.com/@mingjunlu/
https://www.fooish.com/html/
http://www.aspphp.online/
http://www.study-area.org/
https://www.cnblogs.com/
https://dotblogs.com.tw/
http://dept.pjhs.tyc.edu.tw/
http://itchen.class.kmu.edu.
http://www.perfume.com.tw/
http://itchen.class.kmu.edu.
https://w3.nhps.tp.edu.tw/
https://sdwh.dev/posts/2020/
https://blogs.iis.net/nazim/
https://medium.com/@mingjunlu/
https://www.fooish.com/html/
http://www.aspphp.online/
http://www.study-area.org/
https://www.cnblogs.com/
https://dotblogs.com.tw/
http://dept.pjhs.tyc.edu.tw/
http://itchen.class.kmu.edu.
http://www.perfume.com.tw/
http://itchen.class.kmu.edu.
https://w3.nhps.tp.edu.tw/
https://sdwh.dev/posts/2020/
https://blogs.iis.net/nazim/





留言
張貼留言