Module 2: Security Requirements Gathering
1.In the Derived Approach, what we don't include?
A) Abuse Case
B) Security Use Case
C) Abuse Stories
D) Octave
Octave (Operationally Critical Threat, Asset, and Vulnerability Evaluation), a risk-based strategic assessment and planning technique, is not included in the Derived Approach for system security.
2.Abuse Case is derived from______.
A) Use Case
B) Abuse Case
C) Security Use Case
D) Abuse Stories
Abuse Case is a derivative of Use Case. It refers to a scenario where an application may be used in harmful ways by adversaries. So, it is derived from the Use Case by testing the extent to which it can be exploited.
A Security Use Case deals with potential security threats, it doesn't give the scenarios in which an application can be used unfavorably. Hence, it can't be the origin of an Abuse Case.
Abuse Stories, like User Stories in agile development, detail nefarious actions towards a software system. However, they aren't used to derive an Abuse Case; instead, they are more of a narrative of a hypothetical abuse scenario.
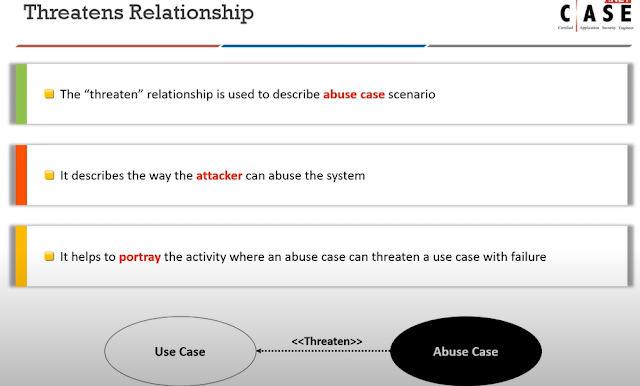
3.The threaten relationship is used to describe________
A) Use Case
B) Abuse Case
C) Security Use Case
D) Abuse Stories
The threaten relationship is used to describe the relationship between an attacker and a system. It is used to identify the potential threats that an attacker may pose to a system. An abuse case is a specific type of threat relationship that describes a particular attack scenario. It is used to identify the steps an attacker may take to exploit a system and the potential consequences of the attack.
4.Which of the following relationship is used to describe security use case scenario?
A. Threatens Relationship
B. Extend Relationship
C. Mitigates Relationship
D. Include Relationship
以下競價系統的Use Case示意圖
其中Etends屬於來自Security Use Case反向箭頭
5.Ted is an application security engineer who ensures application security activities are being followed during the entire lifecycle of the project. One day, he was analyzing various interactions of users depicted in the use cases of the project under inception. Based on the use case in hand, he started depicting the scenarios where attacker could misuse the application. Can you identify the activity on which Ted is working?
A. Ted was depicting abuse cases
B. Ted was depicting abstract use cases
C. Ted was depicting lower-level use cases
D. Ted was depicting security use cases
6.Which of the following can be derived from abuse cases to elicit security requirements for
software system?
A. Misuse cases
B. Data flow diagram
C. Use cases
D. Security use cases
7.Which of the following relationship is used to describe abuse case scenarios?
A. Include Relationship
B. Threatens Relationship
C. Extend Relationship
D. Mitigates Relationship
8.What is the purpose of abuse case modeling in security requirement gathering?
Response:
A. To identify potential ways an attacker could compromise the system
B. To enhance the system's performance under stress
C. To improve the user interface design
D. To benchmark the system against competitors
Ref:










留言
張貼留言